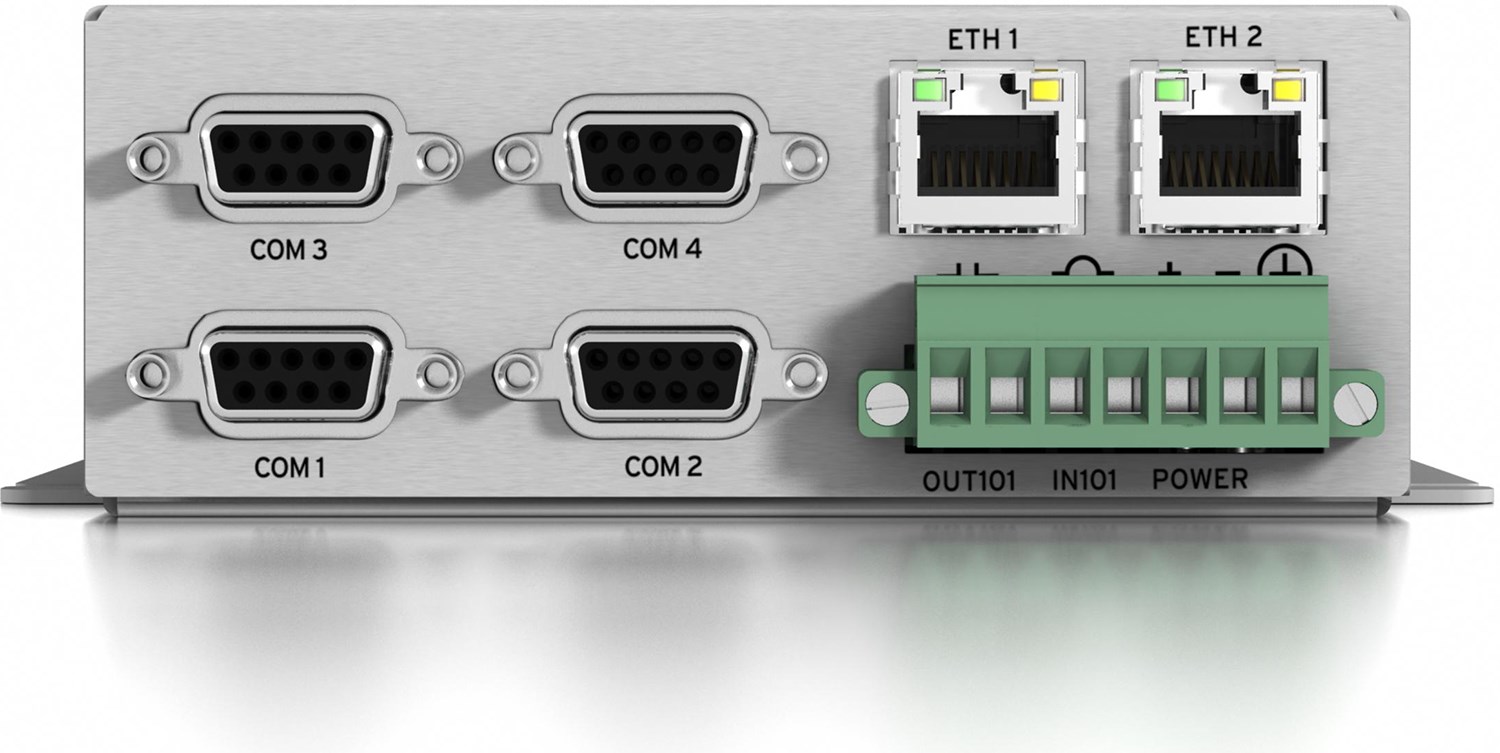
SEL-3622
Security Gateway
A router, VPN endpoint, and firewall device, the SEL-3622 Security Gateway can perform secure and proxy user access for a small number of serial- and Ethernet-based IEDs. The SEL-3622 helps create a user audit trail through strong, centralized, user-based authentication and authorization to modern and legacy IEDs. The SEL-3622 secures your control system communications with a stateful deny-by-default firewall, strong cryptographic protocols, and logs for system awareness. The SEL-3622 also manages protected IED passwords, ensuring that passwords are changed regularly and conform to complexity rules. The SEL-3622 supports enhanced security, enabling you to protect critical cyberassets with strong multifactor authentication technologies, such as RSA SecurID using Remote Authentication Dial-In User Service (RADIUS). With four IPsec profiles available, including 2022 Secure, which contains updated cipher suites, the SEL-3622 offers best-in-class encryption and authentication of information packets.
The SEL-3622 resists known and unknown malware attacks with exe-GUARD embedded antivirus technology. Powerful rootkit resistance, embedded Linux mandatory access controls, and process allowlisting help mitigate attacks against the gateway itself and eliminate costly patch management and antivirus signature updates. The SEL-3622 supports NERC CIP v3 and v5 compliance efforts without needing Technical Feasibility Exceptions (TFEs).
The SEL-3622 integrates physical awareness sensors through an onboard accelerometer, light sensor, and input contact sensor. The SEL-3622 also alerts when Ethernet cables are connected or disconnected, alerting operators to potential remote cyberattacks or physical equipment manipulation.
The SEL-3622 supports SEL-5827 Virtual Connect Client and SEL-5828 Virtual Port Service Software. These applications are provided for free by SEL to make remote SEL-3622 ports available for existing software and terminal applications on your PC, including those using Modbus TCP/RTU.
The SEL-3622 was designed and built in cooperation with the U.S. Department of Energy National SCADA Test Bed and the following companies:
- Schweitzer Engineering Laboratories, Inc.
- EnerNex Corporation
- Tennessee Valley Authority
- Sandia National Laboratories
Starting At
$1,090Centralized Access to Relays and IEDs—Provide a central point of entry to critical cyberassets with user-based access controls and detailed activity logs. Log onto the SEL-3620, not individual IEDs. Manage user accounts and group memberships centrally using Lightweight Directory Access Protocol (LDAP)-accessible systems, such as Microsoft Active Directory. RADIUS functionality enables the use of multifactor authentication systems, such as RSA tokens.
IED Password Management—Enforce strong passwords on IEDs, and change the passwords automatically on a configurable schedule. Satisfy regulatory password requirements, and ensure that no weak or default passwords are in use. Manage passwords on IEDs that use command-line interfaces and on devices that use the Modbus protocol, such as GE UR series relays. At the same time, simplify device access with device checkout and common persistent passwords.
Substation Firewall and IPsec VPN Endpoint—Secure your substation network from malicious traffic with a powerful deny-by-default firewall. Manage status and configuration with an intuitive, menu-driven interface. Securely connect critical networks to the control center using Internet Protocol Security (IPsec) VPNs. Use X.509 certificates with Online Certificate Status Protocol (OCSP) to centrally manage trust.
Accurate Time Synchronization—Synchronize timing information even if a GPS satellite signal is temporarily unavailable. Sync with local communications processors, computers, and security devices using IRIG-B for synchrophasor-accurate timing and Network Time Protocol (NTP) over Ethernet for granular logging and event timing.
Secure Ethernet Communications—Use Media Access Control Security (MACsec) to enhance the existing cybersecurity of the SEL-651R and SEL-651RA recloser controls and reduce operation and maintenance expenses. MACsec secures Ethernet traffic (except IEC 61850 GOOSE and Parallel Redundancy Protocol traffic) between an SEL-651R/651RA and SEL-3622 or Key Server MACsec-enabled routers/radios, providing confidential communication and maintaining message integrity between devices. Key management is automated via the MACsec Key Agreement (MKA) to simplify commissioning and improve the overall user experience.
Virtual Software Client Support—Transform unsecure serial or legacy Ethernet communications on Windows computers to cryptographically secure channels by using SEL-5827 or SEL-5828. These applications are provided for free by SEL to make remote Security Gateway ports available for existing software and terminal applications on your PC, including those using Modbus TCP/RTU. Data are secured using Secure Shell (SSH) with remote port groups, master ports, and serial ports.
Strong Auditability Supports NERC CIP Requirements—Log and time-stamp user access and all commands entered on critical IEDs. Integrate event records into existing log management systems using Syslog. Protect IEDs with strong passwords, and block shared or default accounts. Granular access controls limit users' access to their assigned roles on individual IEDs. Generate specific reports for user activity, user accounts on the device, network ports and services, IED password updates, and password updates
Embedded Antivirus Algorithms—Resist known and unknown malware attacks against SEL Security Gateways with exe-GUARD embedded antivirus. Powerful rootkit resistance technology, embedded Linux mandatory access controls, and process allowlisting help mitigate attacks against the gateways themselves without additional settings or patch management requirements.
Physical Security Protections—Alert on possible malicious physical activity with physical sensor components on the SEL-3622. The SEL-3622 can detect sudden movement (through an embedded accelerometer), sudden changes in visible light (through an embedded light sensor), the opening of cabinet doors (through an input sensor), and the connection and disconnection of Ethernet cables.
Details
Physical Security Protections
Alert on possible malicious physical activity with a physical sensor components on the SEL-3622. The SEL-3622 can detect sudden movement (through an embedded accelerometer), sudden changes in visible light (through an embedded light sensor), the opening of cabinet doors (through an input sensor), and the connection and disconnection of Ethernet cables.
Secured Proxy Access to Relays and IEDs
Use the SEL-3622 to provide a central point of entry to critical cyberassets, including those from SEL and others, with user-based access control and detailed activity logs.
IED Password Management
Enforce strong passwords on IEDs, and have them automatically changed on a configurable schedule. Satisfy regulatory password requirements, and ensure that no weak or default passwords are in use.
Substation Firewall
Secure your substation network from malicious traffic with a powerful deny-by-default firewall. Manage status and configuration with an intuitive, menu-driven web interface. Use virtual local-area networks (VLANs) to segregate traffic and improve network organization and performance.
Routing and NAT
Forward communications among separate Ethernet networks with static routes. The device supports Network Address Translation (NAT) for a wide variety of dynamic network applications. Port forwarding enables the use of a similar remote address space without redesigning IP subnets, and the outbound NAT supports Internet access for those applications that require it.
IPsec VPN
Integrate with existing IT and control systems over VPN tunnels that are secured using IPsec. Use X.509 certificates with Online Certificate Status Protocol (OCSP) to centrally manage VPN trust.
Exe-GUARD Allowlist Antivirus
Protect against known and unknown malware with embedded allowlist antivirus. Reduce patch cycles and resist zero-day attacks without additional settings.
Analog Bit-Based Protocol Conversion
Transform Conitel and other bit-based protocols to Ethernet, and reduce reliance on expensive analog circuits.
User Activity Reports
Log and time-stamp user access events and every command. Integrate event records into existing log management systems using Syslog.
Single Sign-On
Log on to the SEL-3622, not individual IEDs. Users have a single account and password to remember—their own. Manage user accounts and group memberships centrally using LDAP-accessible systems, such as Microsoft Active Directory, or RADIUS. RADIUS allows you to enhance security with multifactor authentication, such as RSA SecurID.
Support NERC CIP Requirements
Implement strong user-based access controls to the electronic security perimeter (ESP) while protecting IEDs with strong passwords and blocking shared or default accounts. Granular access controls limit users' access to their assigned roles on individual IEDs.
Industry-Vetted Security and Interoperability
- IRIG-B time synchronization receives and distributes the IRIG-B signal to maintain time synchronization.
- X.509 certificates ensure strong authentication for incoming connection requests.
- OCSP certificate revocation operates with standard certificate servers to centrally revoke certificates and prevent unwanted connections.
- HTTPS web interface allows convenient, secure setup and management and eliminates the need for extra PC software.
- Syslog logs events for consistency and compatibility and enables centralized collection.
- IPsec (RFC 4301, 4302, 4303) creates a secure VPN.
- Lemnos interoperability facilitates communications between Cisco routers and Lemnos-compliant devices.
Virtual Software Client Support
Transform unsecured serial or legacy Ethernet communications on Windows computers to cryptographically secure channels by using SEL-5827 or SEL-5828 Software. These applications are provided for free by SEL to make remote SEL-3622 ports available for existing software and terminal applications on your PC, including those using Modbus TCP/RTU. Data are secured using SSH with SEL-3622 port groups, master ports, and serial ports.

- Cybersecurity and physical security of remote electronic devices
- IED password management
- Firewall and IPsec VPN endpoint
Minimum Software Version
Video Playlists
How to set the SEL-3620 & SEL-3622 Security Gateways
- How to set the SEL-3620 and SEL-3622 Security Gateways: Series Introduction
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 1—Initial Configuration
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 2—Group Privileges
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 3—Command Line Tools
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 4—QuickSet Proxy
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 5—Virtual Port Access
- How to set the SEL-3620 and SEL-3622 Security Gateways: Part 6—Proxy Logs and Reports
- Establishing MACsec Automatic Commissioning Mode
- Establishing MACsec Manual Commissioning Mode
Latest Firmware Versions
There are no firmware versions available for this product.
| Product | Revision | Firmware ID | Date Available | Serial Number |
|---|---|---|---|---|
| SEL-3622 | R215-V0 | SEL-3622-R215-V0-Z018006-D20241001 | 10/3/24 | ~1242770001 |
The Firmware IDs for older versions of the firmware can typically be found in Appendix A of the instruction manual.
Minimum Software Version
Sales Resource Central access is required to view the content in this tab.
Sales Resource Central3620 3622 3610 - Software Tab
Configuration Software
SEL-5827 Virtual Connect Client
SEL-5827 supports the SEL-3610 Port Server, SEL-3620 Ethernet Security Gateway, and SEL-3622 Security Gateway. SEL provides this software at no cost to transform unsecured serial or legacy Ethernet communications on Microsoft Windows to cryptographically secure channels.
Learn more and download here.
SEL-5828 Virtual Port Service
SEL-5258 supports the SEL-3610 Port Server, SEL-3620 Ethernet Security Gateway, and SEL-3622 Security Gateway. SEL provides this software at no cost to transform unsecured serial or legacy Ethernet communications on Microsoft Windows to cryptographically secure channels.
Learn more and download here.